Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

As digital finance rapidly evolves, concerns about privacy, personal freedom, and financial sovereignty have moved to the forefront especially for anyone managing cryptocurrencies in 2025. Anonymous crypto wallets have emerged as a crucial tool, offering users a way to control digital assets while minimizing personal data exposure.
Unlike traditional wallets that often require formal ID checks and ongoing tracking, these solutions put user privacy before all else.
For activists, citizens in restrictive regimes, or even regular users tired of endless data collection, the appeal is clear: send and receive crypto without revealing your identity or leaving an obvious trail. Even as surveys report that over 60% of global crypto holders cite privacy as a leading concern (Chainalysis, 2024), more people are seeking robust, anonymous wallet options.
n this guide, we’ll break down exactly what sets anonymous wallets apart, how they work, and which options might best serve your needs in the future landscape of crypto.
An anonymous crypto wallet allows you to manage, send, and receive digital currencies in a way that makes it extremely difficult for outsiders even blockchain analytics firms to link transactions to your real-world identity. Unlike most regular wallets (which are often tied to centralized exchanges requiring name and ID) or so-called “pseudonymous wallets” (which don’t ask for ID but still leave transaction trails that can be deanonymized), true anonymous wallets focus on enabling privacy from the ground up.

The core user goals are clear: maintain freedom, safeguard your financial movements, and protect yourself from censorship or unwanted surveillance. For example, activists may use these wallets to organize funding without risk of exposure, while everyday users leverage them to simply stay off the radar.
| Anonymous Wallet | Regular Wallet | Pseudonymous Wallet | |
|---|---|---|---|
| Registration | No | Yes | No |
| KYC Required | No | Yes | No |
| Privacy Tools | Yes (ex: CoinJoin) | No | Limited |
| User Data Exposure | Minimal | Full | Partial |
| Example Use | Organizer in high-risk region | Investor on mainstream exchange | Basic BTC mobile app user |
Privacy technologies play a crucial role. For instance, wallets like Wasabi use CoinJoin to combine many transactions together, scrambling inputs and outputs so outside parties can’t easily determine who sent what to whom. Others offer “air-gapping”—keeping signing devices offline to shield private data from online hacks. Meanwhile, running wallets over Tor or a VPN helps obscure your network fingerprint, further enhancing on-chain and off-chain privacy.

It’s important to distinguish technical privacy (the features and protocols built into the wallet) from practical privacy (how users’ real-world habits affect their anonymity). For example, even with robust privacy tech, reusing addresses or exposing metadata on a compromised device could still reveal your identity.
A popular case: the Wasabi Wallet CoinJoin system, which has helped thousands increase Bitcoin transaction privacy, but its effectiveness depends on users following best privacy practices.

When evaluating an anonymous wallet for 2025, consider this checklist:
| Criteria | Requirement |
|---|---|
| No KYC | ✔ |
| Open-source | ✔ |
| Supports privacy coins | ✔ |
| Integrated privacy tech | ✔ |
| Metadata minimized | ✔ |
| Tor/VPN option | ✔ |
| Seed backup control | ✔ |
| Regular audits | ✔ |
Leading privacy coins like Monero and Zcash, as well as Bitcoin wallets with built-in mixing, are setting industry standards for what effective anonymity looks like in practice.
Xem thêm:
Each type offers a distinct privacy and usability profile. Software wallets deliver strong privacy features out of the box and seamless integration with privacy coins. Hardware wallets, while excellent for cold storage, require careful setup to keep transactions anonymous. Paper and air-gapped wallets provide the highest protection from online threats, but can be trickier for frequent use or backups.
| Type | Setup Requirements | Supported Coins | Anonymity Features |
|---|---|---|---|
| Software | App install & backup | BTC, XMR, ZEC, more | CoinJoin, mix networks, stealth addrs |
| Hardware | Device purchase, config | Multi-asset | Offline storage, some privacy tools |
| Paper | Manual generate/print | BTC, XMR manually | No digital footprint |
| Air-Gapped | Advanced, DIY setup | BTC, XMR, ZEC | Fully offline signing |

| Wallet | Platform | Privacy Features | Supported Coins | Usability |
|---|---|---|---|---|
| Wasabi | Win/Mac/Linux | CoinJoin, Tor, no KYC | BTC | Tech-savvy friendly |
| Samourai | Android | Whirlpool, Tor, Ricochet | BTC | Intermediate |
| Best Wallet | All | Mixing, stealth, MPC | BTC, ETH, XMR, more | Intuitive |
| Zengo | iOS, Android | MPC, no keys, biometric | 25+ assets | Beginner |
| Exodus | Desktop, Mobile | No KYC, privacy coin | 200+ | User-friendly |
| Ledger/Coldcard | Hardware | Seed-only, air-gap, privacy coin apps | Multi-asset | Advanced |
| Ellipal/Tangem | Hardware | Air-gapped, QR signing | 100+ | Moderate |
Following privacy-first community guides (like those from the Wasabi or Monero projects) greatly boosts your operational security. Remember: a technically private wallet still requires disciplined user behavior to offer real-world anonymity.
While privacy wallets offer powerful tools, it’s vital to recognize their restrictions. Bitcoin (and most chains) are only pseudonymous: wallets may obscure user data, but skilled analysts can still try to connect transaction dots unless you’re using privacy coins like Monero, which obfuscates all chain data by default.
Main risks include blockchain analytics (specialized firms mapping transaction flows), metadata or IP leaks during use, and “device hygiene” flaws like malware or compromised browsers. Regulatory landscapes are also in flux. While wallets themselves are typically legal in most countries as of 2025, some regions (like the EU/US) are tightening rules around privacy coins and mixing services, demanding caution.
High-profile cases (e.g., the 2023 arrest of mixing service developers) show that even purely technical privacy is vulnerable to aggressive law enforcement or new compliance mandates. It’s also critical to use these tools ethically, respecting local laws and not facilitating illegal activity.
Related reads to deepen your knowledge:
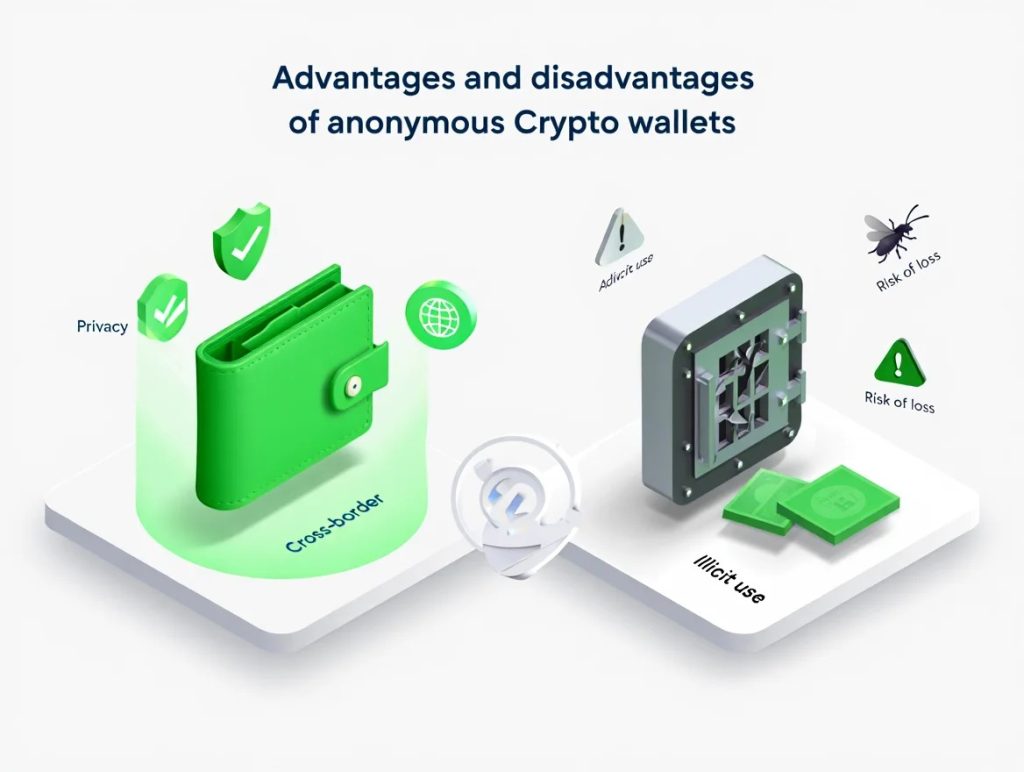
| Advantages | Disadvantages |
|---|---|
| Privacy, freedom, user control, decentralized backup | Usability, support, legal risk, recovery |
Ultimately, anonymous wallets empower but also challenge users: the right fit depends on your privacy needs, risk tolerance, and technical comfort level.
Can I buy cryptocurrencies completely anonymously in 2025? In practice, yes if you use decentralized, non-KYC exchanges or swap services and privacy coins. However, obtaining complete anonymity requires discipline and awareness of potential indirect leaks.
Are anonymous wallets legal? Wallet software is generally legal worldwide, but using privacy coins or mixing in certain countries could attract regulatory attention. Always check current laws in your jurisdiction.
How secure are anonymous wallets? Most offer robust security if you maintain proper seed phrase management and device security. Open-source, community-audited wallets are often safer, but ultimate security depends on your operational practices.
What are the best privacy coins? Monero (XMR), Zcash (ZEC), and Pirate Chain (ARRR) are leading options. Each uses unique cryptographic methods for strong on-chain privacy.
What’s the difference between privacy wallets and regular wallets? Privacy wallets focus on protecting your identity and transaction data, while regular wallets prioritize ease of use and often require identity verification for full functionality.
Choosing the best anonymous crypto wallet often comes down to which features you need most privacy layers, supported coins, and platform compatibility. Use this quick reference for comparison:
| Wallet Name | KYC Requirement | Privacy Tech | Supported Coins | Platform | Ease of Use |
|---|---|---|---|---|---|
| Wasabi | No | CoinJoin, Tor | BTC | Desktop | Intermediate |
| Samourai | No | Whirlpool, Tor | BTC | Android | Intermediate |
| Best Wallet | No | Mixing, stealth, MPC | BTC, ETH, XMR | All | Easy |
| Zengo | No | MPC, encryption | Multi | Mobile | Beginner |
| Exodus | No | Privacy coins, no KYC | Multi | Desktop/Mobile | Easy |
| Ledger/Coldcard | No | Offline, privacy coin compatible | Multi | Hardware | Advanced |
| Ellipal/Tangem | No | Air-gapped signing | Multi | Hardware | Moderate |
The landscape of anonymous crypto wallets in 2025 is rich and varied, reflecting a growing demand for privacy, security, and self-sovereignty in digital finance. By understanding their distinguishing features, technology, and risks, users can make informed choices that suit their specific situations, whether they’re safeguarding personal funds, conducting private transactions, or building a resilient financial toolkit. Always balance privacy benefits with usability and legal awareness as you explore the best wallet for your needs.
Web Tai Chinh is a portal that updates news and information related to finance quickly and accurately, helping users have an overview before investing, clearly understanding concepts and terms related to Finance. Explore more insights in our Cryptocurrency category, start your crypto wallet development journey today with the right partner for long-term success.
📞 Contact: 055 937 9204
✉️ Email: webtaichinhvnvn@gmail.com
📍 Address: 13 Ho Tung Mau, An Binh, Di An, Binh Duong